Windows event logs are a tool that every cybersecurity and IT professional should have in his or her arsenal. They can be used locally for troubleshooting or centralized for network awareness. When utilized centrally, powerful software known as a Security Information Event Management (SIEM) can be utilized to parse and search log files. But what if you are working locally? Is there an efficient method to do the same? You will find the answer to these questions lies in Microsoft’s most powerful tool belt, Microsoft PowerShell.
What are Windows Event Logs?
Windows event logs include a detailed record of system, security, and application notifications that are created and stored by the operating system. In addition to the more well-known logs, additional event logging can also be enabled for a number of specific applications on the system such as Microsoft AppLocker, PowerShell, or Sysmon. Windows event logs are available via the event viewer. To open the event viewer you can either find it within the control panel or type in eventvwr under the run command. Windows event logs are available under the C:\WINDOWS\system32\config\ folder.
Like any standard logging practice, Windows event logs have a standard format. Each event will contain the date, time, user, computer, event ID, source, and type. This standardization makes logs easily searchable with PowerShell by utilizing the Get-WinEvent command.
Get-WinEvent
Get-WinEvent is a PowerShell command-let available in Windows Vista and above. It allows you to gather and search event logs on either local or remote computers. Searchable logs include classic logs, new logs introduced with Windows Vista, and log files generated with Event Tracing for Windows. Multiple logs can be specified with a single command. If you do not specify any parameters, Get-WinEvent will get all the events from all the event logs on the computer. Get-WinEvent is only available in Windows Vista/2008 R2 or higher and requires Microsoft .NET Framework 3.5 or later. The table below outlines all the parameters associated with this command.
| Parameter | Format | Description |
| ListLog | string | This parameter takes a comma separated list of event log names. Wildcards are permitted. A value of * will search all logs. |
| LogName | string | This parameter also takes log names in a comma separated list. |
| ListProvider | This parameter takes a comma separated list of providers, the program or service that writes events to the event log. Wildcards are permitted. A value of * will search all logs. | |
| ProviderName | This parameter takes a comma separated list of providers, the program or service that writes events to the event log. | |
| Path | string | This parameter accepts paths to .evt, evtx, and.etl files in a comma-separated list. |
| MaxEvents | Int64 | This is the maximum number of events that get-winevent will return. The default will return all logs. |
| ComputerName | string |
|
| Credential | PSCredential |
|
| FilterXPath | string | Use an XPath query to select events from one or more logs. |
| FilterXML | XMLDocumentt |
|
| FilterHashTable | hashtable |
|
| Force | Boolean | Required to get debug and analytic logs |
| Oldest | Boolean | This parameter will return the events in oldest-first order. It is required to get events from .etl and .evt files and from debug and analytic logs. |
Some Examples
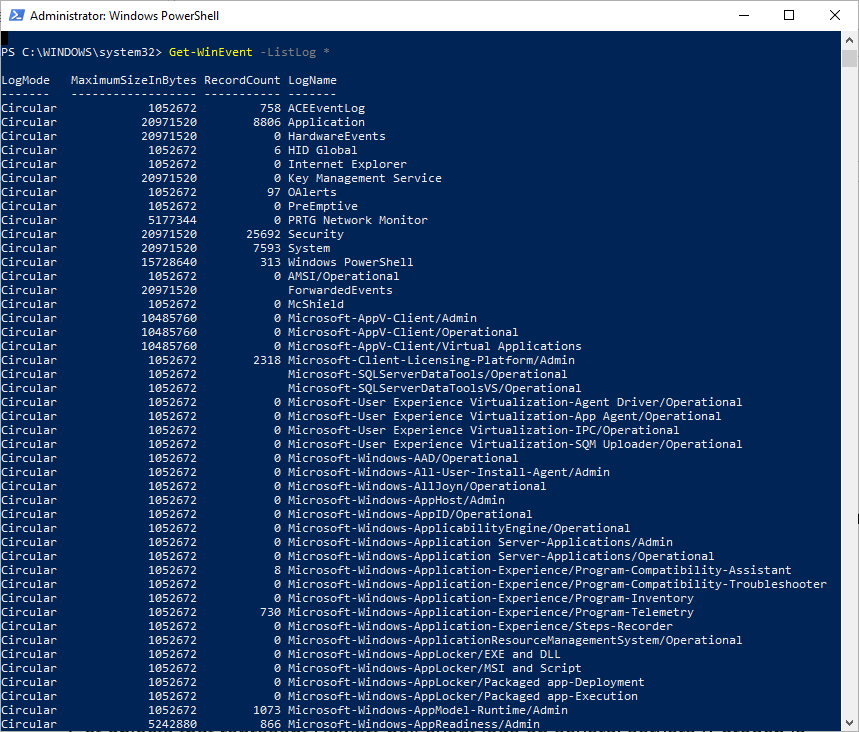
First, to see what logs you have to choose from, utilize the listlog parameter. You will notice the list is very long.
PS C:\> Get-WinEvent -listlog *
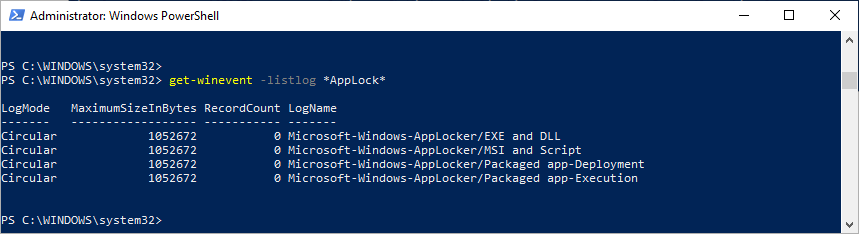
You may wish to narrow it down to all the logs dealing with a particular topic, for example, AppLocker.
PS C:\> get-winevent -listlog *AppLock*
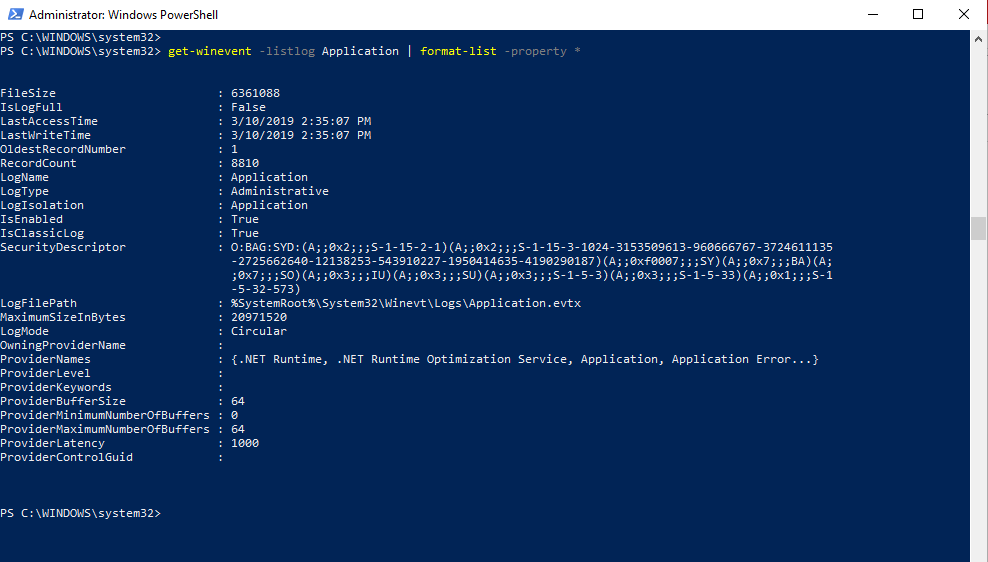
To get all available information related to a single log, such as the Application log, utilize the following command.
To list all the logs on the local machine that contain events, you might do the following.
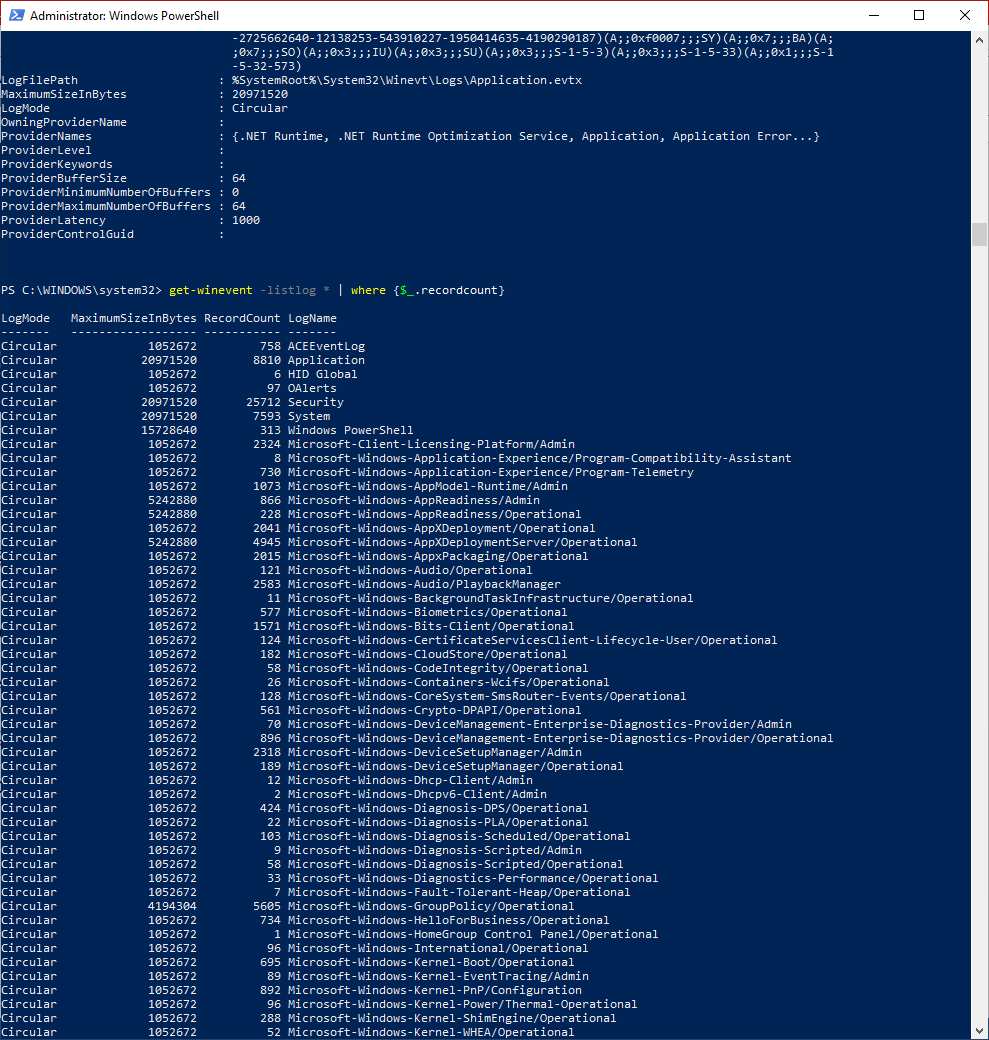
PS C:\> Get-WinEvent -listlog * | where {$_.Recordcount}
You can also search for multiple computers for logs at the same time. This is done with a foreach statement. For example:
PS C:\> $hosts = "Server1", "Server2", "Server3"
PS C:\> foreach ($server in $hosts)
{$server; get-winevent -listlog "Windows PowerShell" -computername $server}
Identifying Brute Force Attacks
Logs on the domain controller may be monitored for multiple failure instances to identify a brute force attack. A domain controller logs a failed Kerberos ticket with log event 4771. An example of a way to investigate a potential brute force attack is to run the command below on a domain controller to look for all failed logins within the last hour.
Get-WinEvent -Filterhashtable @{LogName='Security';id=4771;starttime=(Get-Date).AddHours(-1);endtime=(Get-Date) }
Using Windows Event Tracing
Windows event tracing is a tool utilized by developers to debug their applications. It may be utilized for tracing the shutdown and boot process or for diagnosis such as determining power efficiency of an application. Event trace logs are stored in files with the extension .etl. PowerShell offers an additional methodology for opening or analyzing these trace logs. Be sure to remember to utilize the –Oldest parameter when using Get-WinEvent to parse an event trace log.
PS C:\>Get-WinEvent -Path "C:\Tracing\TraceLog.etl" -Oldest
Windows event logs are extremely easy to search and parse with PowerShell. This is extremely beneficial whether you are monitoring for a particular failure event or a certain type of attack. PowerShell is a handy tool for any cyber defenders arsenal.