If you do any security monitoring, it's easy to get overwhelmed by the amount of events you need to track. You can start by doing longer hours, but eventually you'll end up in a swamp — sucked in to the point that workflow comes to a standstill.
This is the time when you start to use tools and datasets to enrich security events so that you can prioritize and filter events that really matter. There are different approaches, but the one I'm covering is geolocation. That is, of the source of a (network) event.
What Is Geo-IP-Location?
Geolocation, or Geo-IP-location, is a technology that literally gives you the geographical location of an IP address. The "internet" isn't static, so the accuracy of your (geological) information depends on the Geo-IP database you use.
Why You'd Use It
By mapping the sources of your security events you can get more insight into where a threat is coming from. This is useful during, say, a DDoS attack. If you notice the bulk of the traffic is coming from one specific geographical region, you could temporarily put network ACLs that block that traffic. Country-based filtering isn't a good idea on a permanent basis, but it can help (temporarily) survive a DDoS attack sourced from one particular region.
Sources for Geo-IP Data
Where do you get your data from? Any source that provides you with network data as long as it contains source IPs — or destination IPs if you want to check where your traffic is going.
One of the sources is a network monitoring solution, many of which allow you to keep track of the performance and availability of your most critical services. Within WhatsUp Gold network monitoring software, you can also use the netflow data of each machine connected to the company's network. Netflow data provides an excellent source to act as a base for generating Geo-IP data.
If you don't use a network monitoring solution (but you really should), you can use any other log source that includes the IP information. Apache logs have proven to work very well, and you can extract the IPs doing the web requests with:
cat /var/log/apache2/access.log | awk '' > sources.csv
This will give you a list of the sources doing the web request. Depending on your liking you might only be interested in the unique IPs.
cat sources.csv | sort | uniq > sources2.csv
Doing It Manually
One of the most well-known Geo-IP databases are those from Maxmind, which has a paid subscription but also free downloadable databases that sysadmins can use in their existing toolset to enrich event data.
The Automatic Way
Writing your own scripts to do part of the processing manually is great, but you can also automate this process. Once you have a list of IP addresses you can upload them to a service and have them laid out on a geographical map.
One of these automated services is CartoDB, an online application that allows you to map and analyze location data. Before you can start using it you need a file with a set of IP addresses. Keep in mind these are the files you generated previously (don't worry if your file contains other columns; you can select the correct column within CartoDB). Start by signing up to create your account.
Once subscribed, head to Your Datasets and choose New Dataset. Then, you guessed it, upload your datafile (make sure your file has a .csv extension) and choose Connect Dataset. You'll end up on this screen:
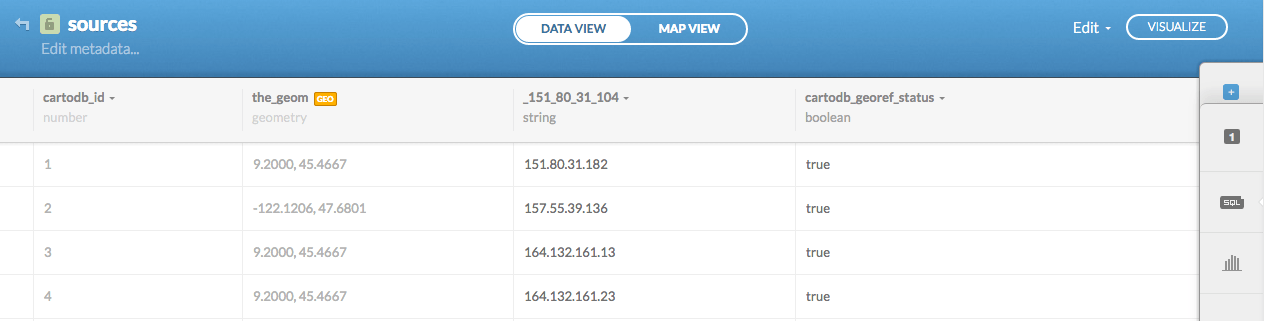
The next step is Visualize the data. You'll get the option to Create the map. Then click on Map view to admire your newly created geomap:
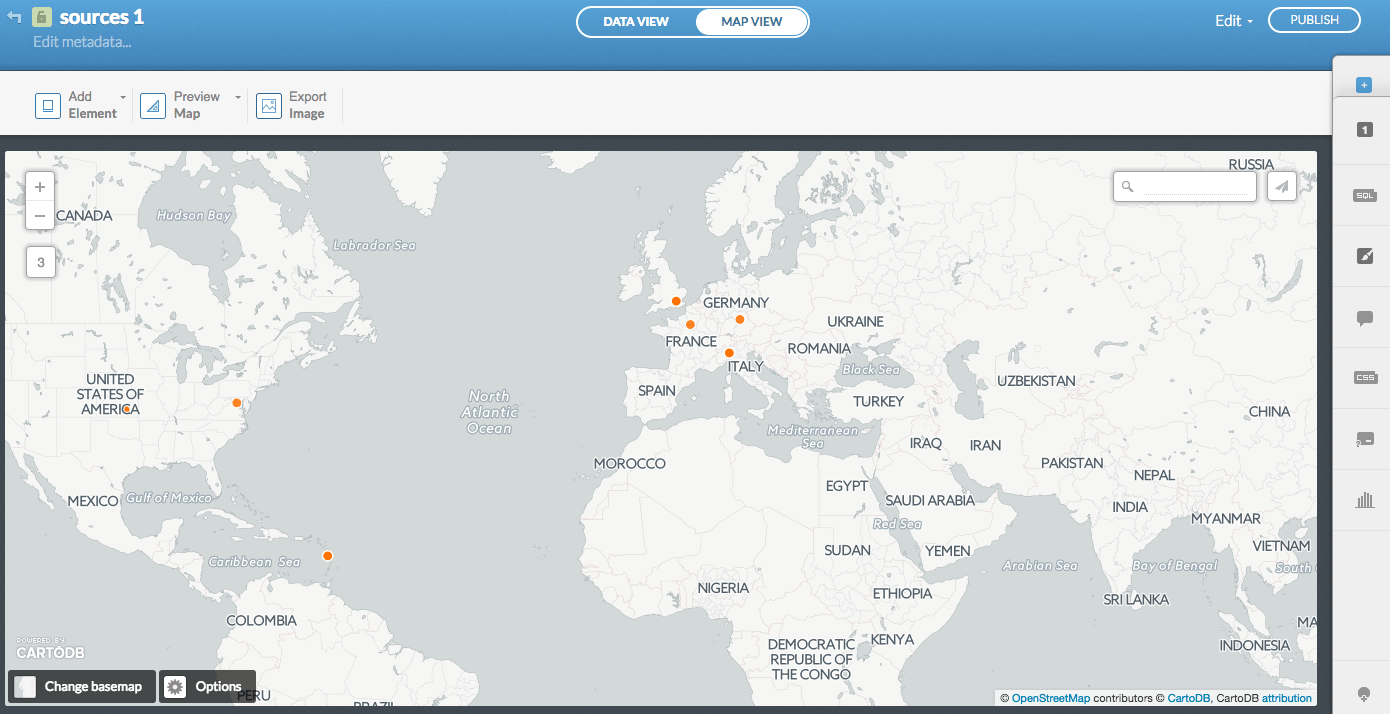
Dashboards
Some dashboards (Kibana from the ELK stack, for instance) can do the geographical representation for you. This is great if the dashboard is connected to your data sources.
If not, you can still use the method described in this post to enrich your security reports.
