If you are a systems administrator or a security engineer, it is probable you have a requirement to filter and forward Windows event logs either directly or hierarchically. There are many alternatives available to accomplish this goal, one of which is Windows Event Forwarding (WEF). In this article, you will learn to configure a simple source initiated WEF subscription which utilizes the HTTP protocol to forward events between a client and a collector in a single domain.
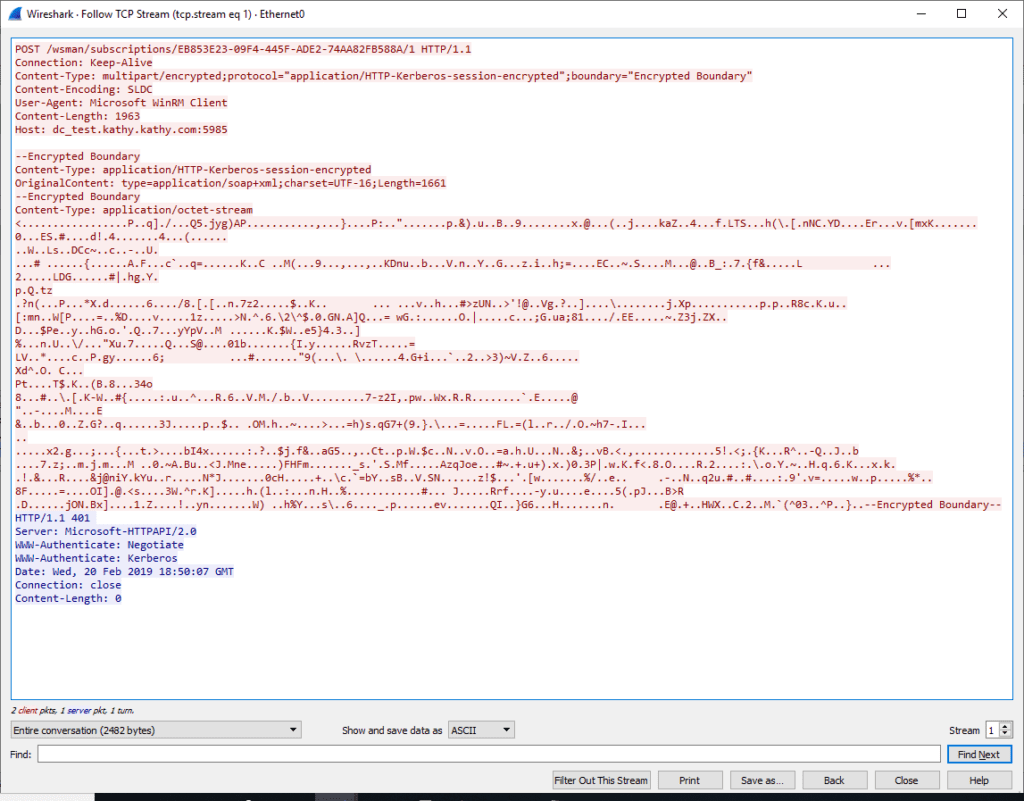
WEF uses Windows Remote Management (WinRM) to natively forward logs from several clients to a single collector. WinRM is Microsoft’s version of WS-Management Protocol. WS-Management is a SOAP-based protocol which allows systems to exchange management information via HTTP or HTTPS. The below Wireshark screen capture is an example of the HTTP exchange. You may observe that although the header information is exchanged in clear text, the actual log payload is encrypted via Kerberos.
Windows Event Forwarding can be an advantageous choice for the forwarding of event traffic within your network for several reasons. First, in a source based subscription, client machines initiate a connection to the subscription without the deployment of any additional software or agents. If new machines join the domain and receive the group policy settings, they will automatically begin forwarding their log traffic. The exchange is via Kerberos, so events are encrypted by default. Windows Event Forwarding offers detailed filtering options that are not natively available in many collectors. In fact, these options can be placed in version controlled XML files for configuration management. Although in this article we will only use the WEF source initiated configuration, there is both a push and pull mode available. Finally, WEF includes options to throttle the speed at which log traffic is forwarded to protect network bandwidth.
Setting Up Windows Event Forwarding
To initiate your WEF subscription, you must first configure a collector. In this example, the WEF collector was set up on a Windows 2012 R2 server.
Configuring a Windows Collector
To set up the collector, first, you must enable the Windows Event Collector Utility (wecutil). To do so, run Windows PowerShell as Administrator, and type the command wecutil qc.
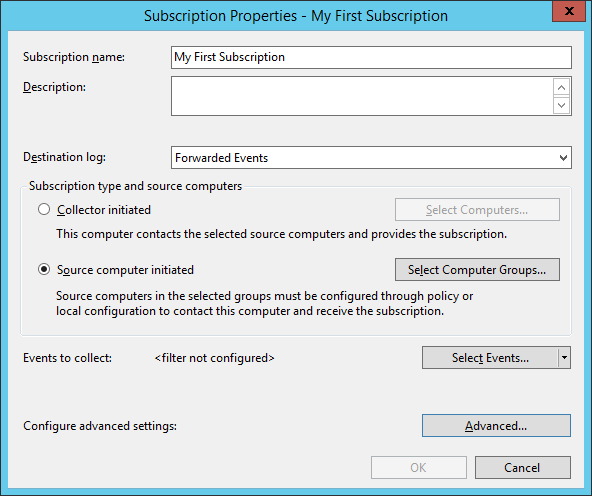
On the collector machine, you will create a subscription. To do so, open eventvwr.msc from the run menu. When Windows Event Viewer opens, highlight subscriptions and choose “Create New Subscription.” In this example, you will configure WEF to forward all categories of events from the application log. Your initial subscription page should look like the one below.
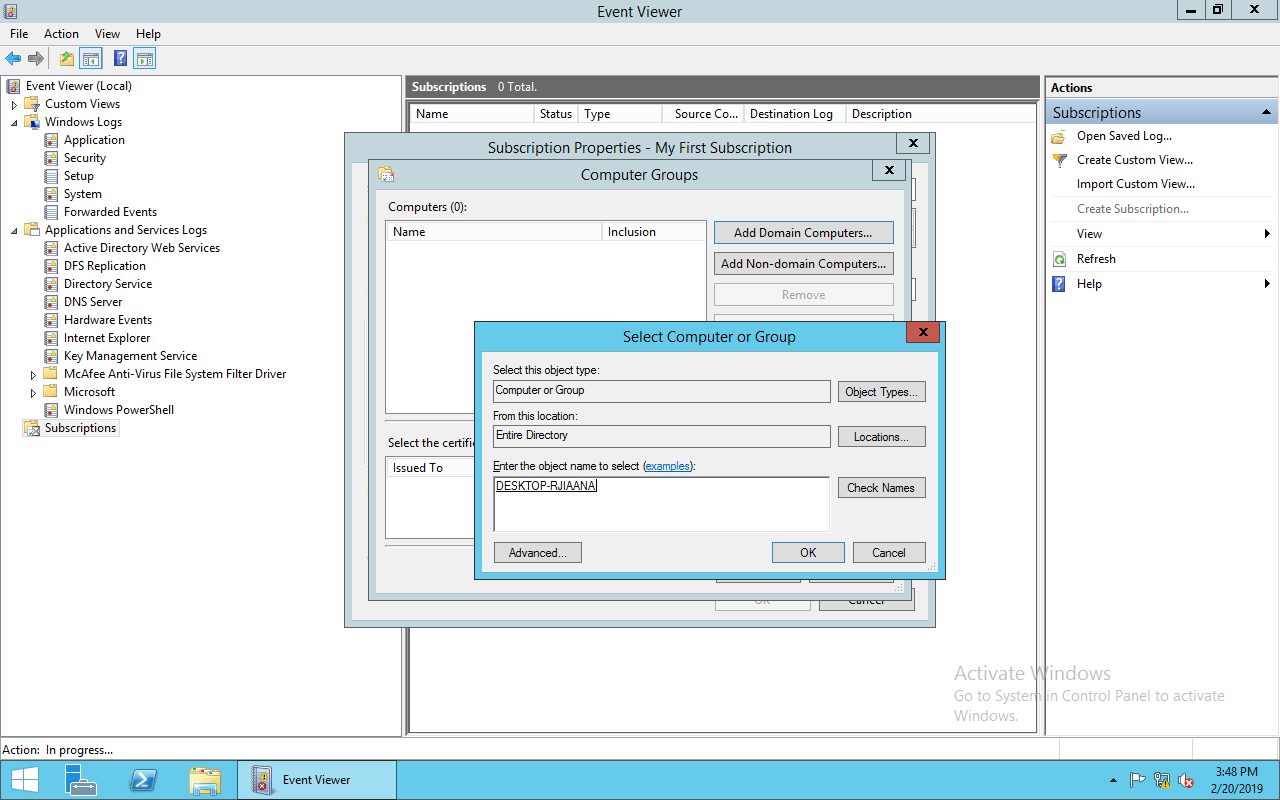
As part of the subscription configuration, you will add any computers or groups that will be utilizing this WEF subscription. Choose the radio button for source computer initiated and hit the button to Select Computer Groups. Add your domain computer or group as shown below.
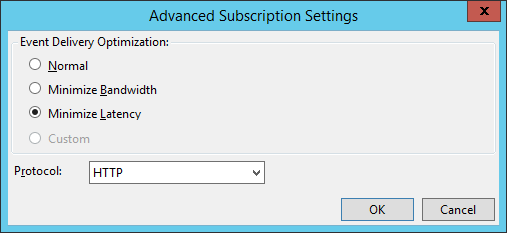
Under advanced settings, set the event delivery optimization to minimize latency, which will send events every 30 seconds. This option was chosen to speed up troubleshooting. If you have a bandwidth constrained environment, you may opt to select minimize bandwidth.
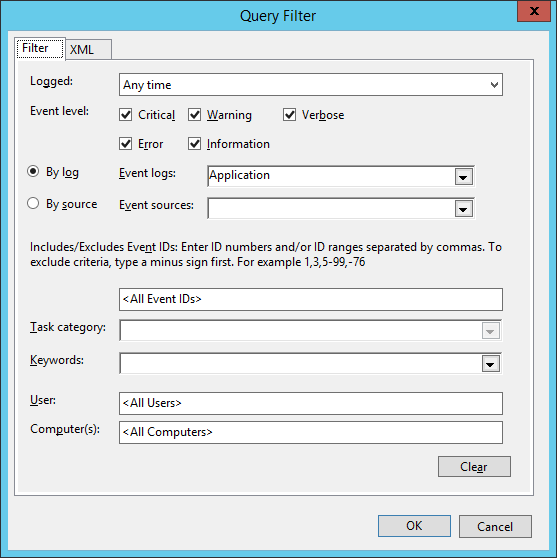
Finally, the subscription must be modified to identify which log traffic will be forwarded. In this example, select by log “Application” and choose all event levels. We now have a working event subscription.
Configuring a Windows Client
Next, we will need to configure our client. Client configuration can be configured entirely through group policy to enable all clients at the same time. Two settings must be enabled in group policy.
- WinRM must be enabled
- The WEF subscription server must be configured.
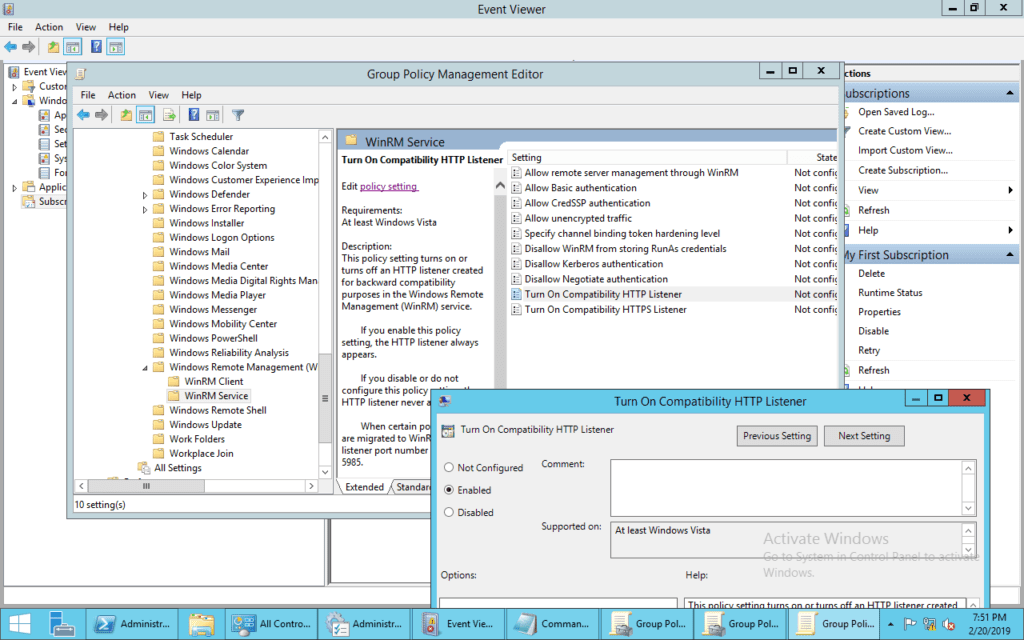
To enable the WinRM server, go to the group policy Management Editor in Active directory. Under “Computer Configuration/Policies/Administrative Templates/Windows Components/Windows Remote Management/WinRM Service/ Turn on Compatibility HTTP Listener” select Enabled.
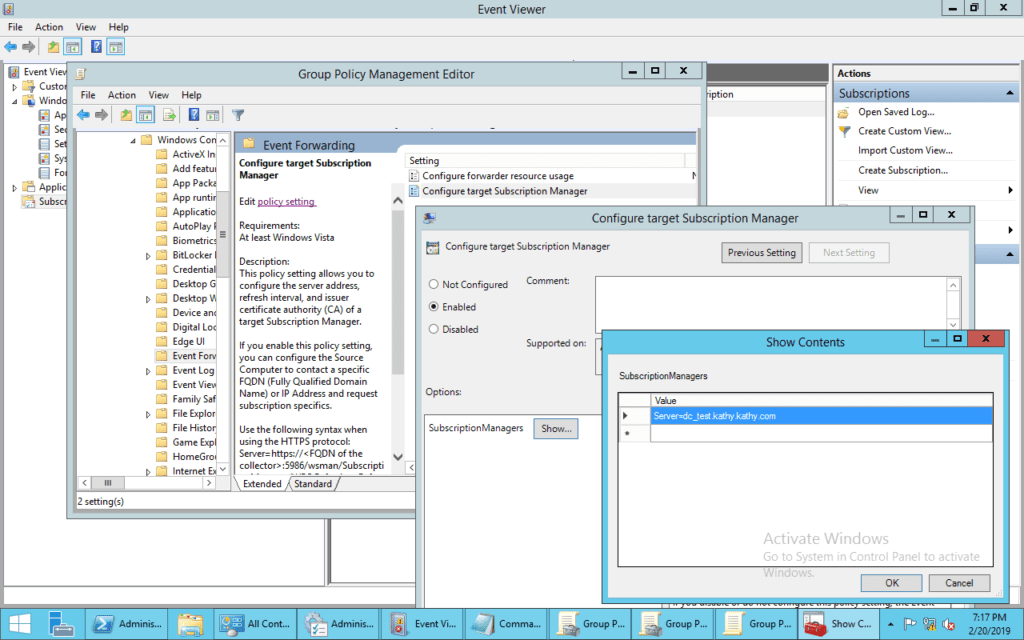
Secondly, to configure the WEF subscription server, go to “Computer Configuration/Policies/Administrative Templates/Windows Components/Event Forwarding/Configure Target Subscription Manager”. Enter your fully qualified server name as follows Server=<collector fqdn>.
Testing the Configuration
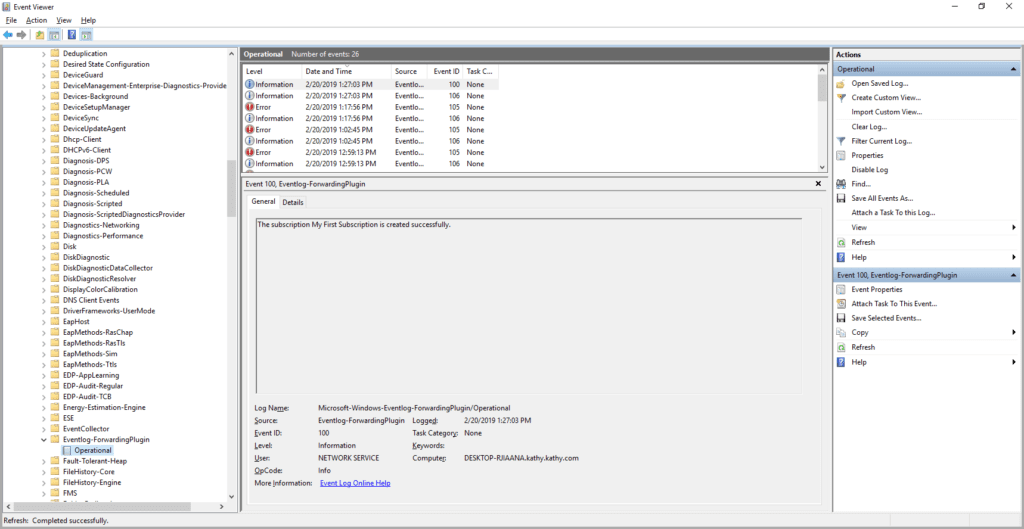
Let’s test this to see if it works. On your client machine, from an administrative command prompt, run the command gpupdate /force to pull down the new policy and open event viewer. If there are any issues, they will show up in the following log file Microsoft-Windows-Eventlog-ForwardingPlugin/Operational. When all is working well you will see event ID 100 which states “The subscription <subscription name> is created successfully.”
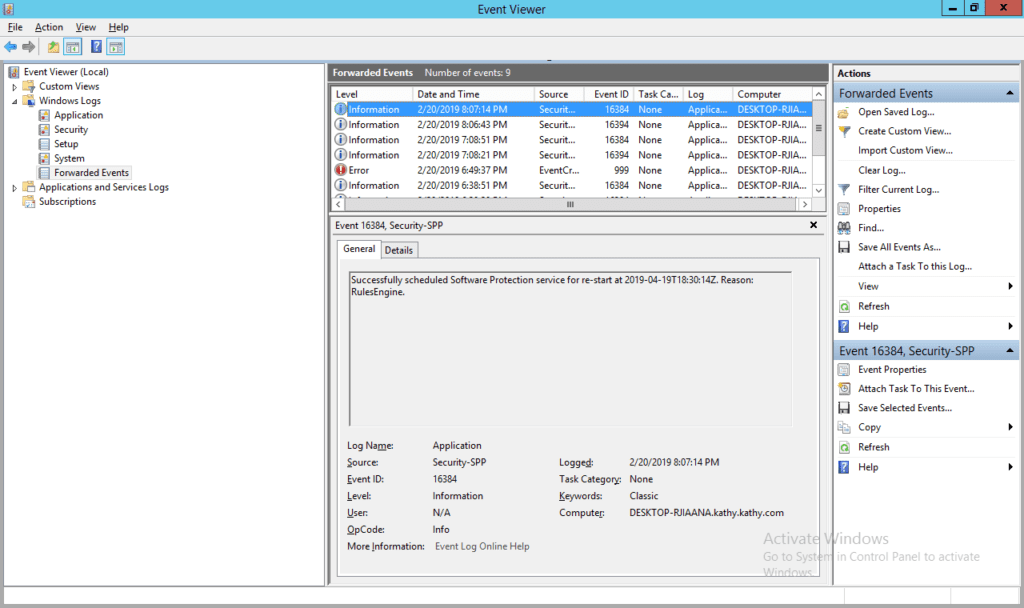
To fully test this feature, you can now generate a test log. Open up a command prompt as administrator and type the following command: eventcreate /id 999 /t error /l application /d "Test event." This will generate a test log in the application event log. Events will arrive in the collector in the Forwarded Events log.
Advanced Options
WEF also offers several more advanced options that can be adjusted to optimize performance. Such options include enabling encrypted TLS, advanced filtering via XML, adding computers outside of the domain via certificate authentication. Tasks can also be added to a particular event to email a user, open an application, or display a message. Finally, log traffic collected with distributed event collectors can be forwarded once again to a SIEM to form a simple event forwarding hierarchy.
Summary
WEF is a useful tool in many environments. If you work with a predominantly windows based architecture including one or many domains, WEF is an effective methodology to centralize logging without any additional software requirements. For additional information on this valuable technology please see the following links.
