The Cisco ASA is one of the most commonly used devices that provides VPN (virtual private network) access to businesses across the globe. If your Cisco ASA is not working as expected, your remote workers may be completely unable to work. As the person-in-charge of ensuring this is working as expected, you want to be notified as soon as possible if there is any problem. In this post, I'll show you how to monitor Cisco ASA VPN with WhatsUp Gold, for a general how-to on VPN monitoring with WUG, check out my community post here.
What is WhatsUp Gold?
WhatsUp Gold is a complete network monitoring solution that allows you to monitor your critical systems, both on-premise and in the cloud. WhatsUp Gold is highly customizable and flexible. With WhatsUp Gold, not only can we monitor the status of Zoom but we can also monitor the availability of your network infrastructure, server infrastructure, storage infrastructure, and much more.
How do I Monitor my Cisco ASA VPN?
WhatsUp Gold allows you to monitor anything that we can populate data about. It doesn't matter if that data is from on-premise systems like your routers, switches, firewalls, and servers or cloud environments such as AWS, Azure, or Meraki as well as SaaS (Software as a Service) solutions such as Zoom, WebEx, or Office 365.
That being said, you will more than likely always have multiple solutions to choose from when solving for “How do I monitor this?”. For Cisco ASA VPN, I would suggest using SNMP traps sent to WhatsUp Gold. WhatsUp Gold accepts SNMP traps using ‘Passive Monitors’. Passive Monitors allow you to listen for SNMP traps, Syslog messages, or Windows Events. You also have the ability to tie back ‘Actions’ to the received passive monitors, which can include everything from simply e-mailing about the problem to running corrective actions using commands sent by WhatsUp Gold’s SSH action.
Configure your device to send traps
By default, your Cisco appliance will not be configured to send SNMP traps. We need to specify where to send our traps, as well as which traps we want to send. I will not be providing you *EXACTLY* what to put in your configuration since it may vary from model and IOS revision – but, I can direct you to one of the proper documentation links from Cisco in order to do so. Cisco’s documentation also includes other SNMP traps you may be interested in using WhatsUp Gold to listen for.
In general, for the monitor in this article to work you need to be sending the desired trap to the WhatsUp Gold server which can be done with this in your configuration:
snmp-server enable traps all
The final configuration will look something along the lines of this:
| ASA1# show run | grep snmp snmp-server host inside 10.225.64.2 community ***** version 2c snmp-server enable traps syslog snmp-server enable traps ipsec start stop snmp-server enable traps entity config-change cpu-temperature chassis-temperature accelerator-temperature snmp-server enable traps memory-threshold snmp-server enable traps interface-threshold snmp-server enable traps remote-access session-threshold-exceeded snmp-server enable traps connection-limit-reached snmp-server enable traps cpu threshold rising snmp-server enable traps ikev2 start stop snmp-server enable traps nat packet-discard snmp-server enable traps config |
As you can see, I have specified where to send my SNMP traps and enabled every single potential SNMP trap the device could send. WhatsUp Gold will automatically discard the ones we are listening for. Note that there are many useful SNMP traps your Cisco devices can produce and WhatsUp Gold can listen for— take this an opportunity to explore the other possibilities as well. One of the more interesting SNMP traps offered here are the ‘config’ traps. This allows you to send WUG a SNMP trap any time a configuration has changed and we can use that to launch Configuration Management action in WhatsUp Gold. We will most likely have a post on that soon, so stayed tuned.
Enable the passive monitor listener(s)
Your first step in getting this type of monitoring setup is ensuring your WhatsUp Gold system has the SNMP trap listener turned on. The SNMP trap listener is off by default – so, if you have never turned it on in the past we start here. If you have already turned on your SNMP trap listener, you can skip to the next step ‘Create the Monitor’.
Turning on the SNMP trap listener is very simple. Login to your WhatsUp Gold’s web interface and then navigate to Settings > System Settings > Passive Monitor Listeners.
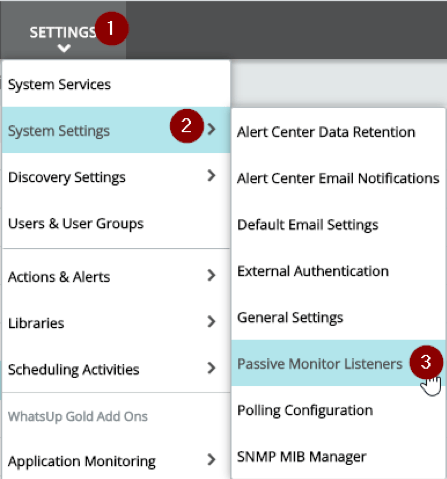
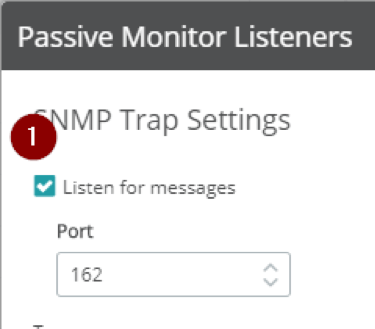
In the Passive Monitor Listeners dialog, check ‘Listen for messages’ under ‘SNMP Trap Settings’, then click Save in the bottom-left corner of the dialog. That’s all – you’ve turned on the listener.
Create the monitor
Now that your SNMP trap listener is on, we need to create an SNMP trap passive monitor in order to have a monitor to associate to the Cisco ASA so WhatsUp Gold knows which SNMP trap(s) we care about saving to the database. By default, any SNMP trap sent to the WhatsUp Gold server we are not specifically telling WhatsUp Gold to listen for will be discarded.
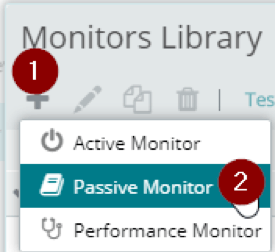
To create the monitor, bring up your Monitor Library by navigating to Settings > Libraries > Monitors. From the Monitors Library dialog, click the + sign, and select ‘Passive Monitor’.
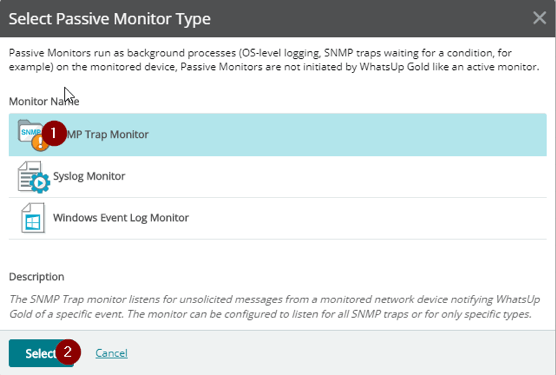
In the Select Passive Monitor Type dialog, click SNMP Trap Monitor then click Select in the bottom-left.
In the Add SNMP Trap Monitor dialog, select ‘Enterprise Specific’ under ‘Generic type (Major)’. Fill in the Enterprise OID with 1.3.6.1.4.1.9.9.171.2.0 -- this is the enterprise OID of Cisco’s cipSecMIBNotifications, which contains all of the traps we care about here. For the ‘Specific type (Minor), I am going to use ‘Any’ in the example. This means regardless of which trap is sent, if the traps objectID starts with 1.3.6.1.4.1.9.9.171.2.0 this monitor will catch it. You can also create specific monitors for each specific condition if you’d like, by using a single digit 1-13 in the ‘Specific type (Minor)’ section. For example, if I wanted a monitor just for ‘cikeTunnelStop’ I would put a 2.
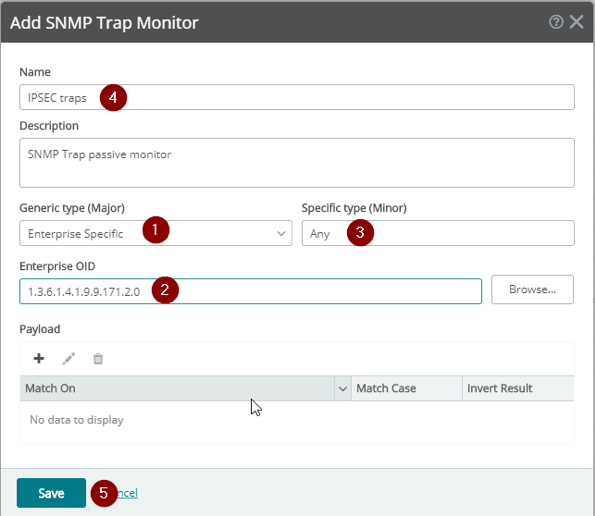
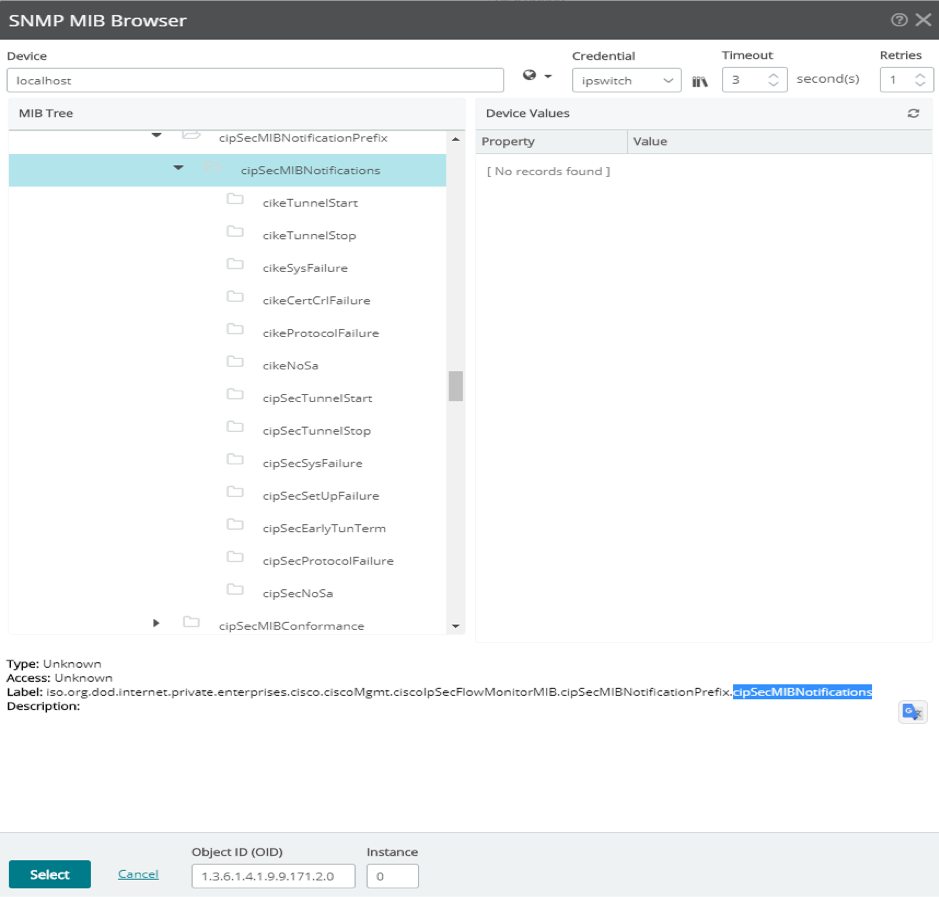
If you click ‘Browse’, you will see all of the following SNMP trap definitions and their associated ‘minor’ number. I will put a quick list here for easy reference:
- cikeTunnelStart: This notification is generated when an IPsec Phase-1 IKE Tunnel becomes active
- cikeTunnelStop: This notification is generated when an IPsec Phase-1 IKE Tunnel becomes inactive
- cikeSysFailure: This notification is generated when the processing for an IPsec Phase-1 IKE Tunnel experiences an internal or system capacity error.
- cikeCertCrlFailure: This notification is generated when the processing for an IPsec Phase-1 IKE Tunnel experiences a Certificate or a Certificate Revoke List (CRL) related error.
- cikeProtocolFailure: This notification is generated when the processing for an IPsec Phase-1 IKE Tunnel experiences a protocol related error.
- cikeNoSa: This notification is generated when the processing for an IPsec Phase-1 IKE Tunnel experiences a non-existent security association error.
- cipSecTunnelStart:This notification is generated when an IPsec Phase-2 Tunnel becomes active.
- cipSecTunnelStop: This notification is generated when an IPsec Phase-2 Tunnel becomes inactive.
- cipSecSysFailure: This notification is generated when the processing for an IPsec Phase-2 Tunnel experiences an internal or system capacity error.
- cipSecSetUpFailure: This notification is generated when the setup for an IPsec Phase-2 Tunnel fails.
- cipSecEarlyTunTerm: This notification is generated when an an IPsec Phase-2 Tunnel is terminated earily or before expected.
- cipSecProtocolFailure: This notification is generated when the processing for an IPsec Phase-2 Tunnel experiences a protocol related error.
- cipSecNoSa: This notification is generated when the processing for an IPsec Phase-2 Tunnel experiences a non-existent security association error.
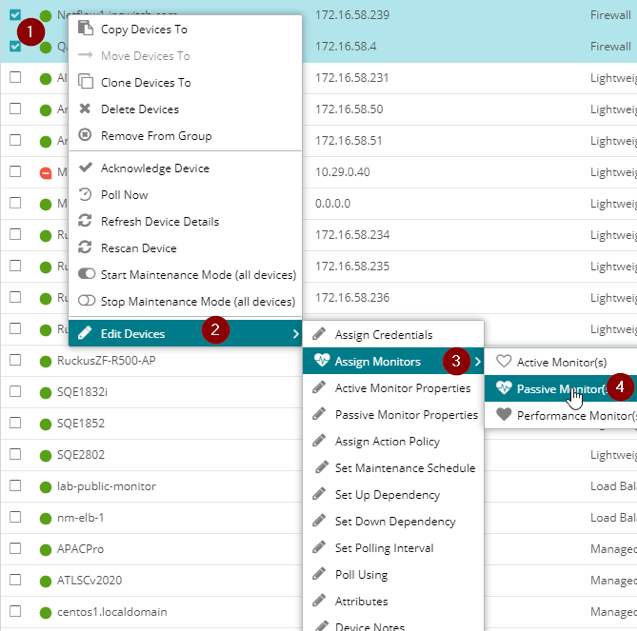
Assign the monitor to your device
Once your monitor (or monitors) have been created, simply assign the monitor to the proper devices. You can do so in bulk from ‘My Network’. Go to a group or use filters to show the devices you want to add the monitor to, select them, right-click one of the devices and navigate to Edit Devices > Assign Monitor > Passive Monitor.
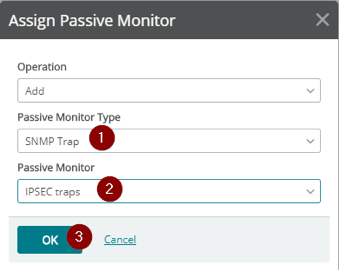
In the next dialog select SNMP trap as the ‘Passive Monitor Type’, select the passive monitor you just created, and then click OK. Your devices are now listening for these traps!
Test your monitor
Well, it’s a bit harder to test passive monitors. Since WhatsUp Gold is listening for a message as opposed to going out and actively checking something (ala active monitors), we need to simulate the actual event occurring somehow. Perhaps you could, for example, create a test tunnel, then start/stop it. I am not an expert on Cisco configurations by any means, so your best bet would be talking with Cisco support if necessary.
So what exactly does this monitor do?
Basically, any time the status of your VPN tunnels change or fail for any reason an SNMP trap will be sent to WhatsUp Gold and we could either alert (ex: e-mail action, SMS action), perform a corrective action (ex: SSH action, PowerShell action), or even a combination of both.
Final notes
You could also leverage WhatsUp Gold’s Device Roles to automatically add this passive monitor to your firewalls as need be. You can do this either by modifying the built-in firewall sub-role, or creating your own role/sub-role if you’d like. We will have another post in the future about Device Roles in general.
What else?
Well, you now have the ability to associate actions with your monitor. Actions can include e-mails, text messages, and much more. Remember this is just *ONE* of *MANY* different ways to accomplish this within WhatsUp Gold. I could, for example, look at individual statistics specific to each tunnel or even individual user statistics. I can go on and on here, but we’ll leave it at that for now. Happy Monitoring!
