One of the more disheartening aspects of log collection within the Windows Operating system are the limited number of out of the box events related to security. It is often desirable to capture any unknown or malicious running processes, capture the source process for outbound connections, identify modifications to files and the registry, and to capture command and PowerShell commands that are run on a particular endpoint. Luckily for systems administrators, Microsoft provides a great tool for this type of log capture within the SysInternals suite called system monitor, or Sysmon.
With the default configuration, Sysmon will fill up your event viewer with log events extremely quickly. As such, tuning of these events to eliminate false positives is critical. Sysmon events can be filtered by adjusting the configuration in the config.xml file. The schema version for the configuration file will need to match the schema for that version of Sysmon. To display the schema version utilize the Sysmon.exe –s option.
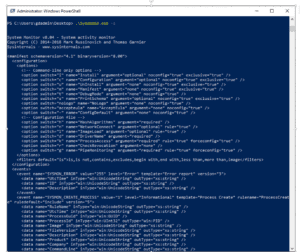
In this case, we will begin our filtering file with the line:
<Sysmon schemaversion="4.1">
You can also choose the hash algorithm that you wish syslog to utilize for hash values.
<HashAlgorithms>MD5</HashAlgorithms>
Start your event filtering with the command
<EventFiltering>
If you use an “include” or “exclude” statement without a filter, it has the opposite effect. For example, the statement below instructs Sysmon to log all “ProcessCreate” events and not to log any “FileCreateTime” events. Any event types not included in the filter will automatically be included.
<Sysmon schemaversion=”4.1”> <EventFiltering> <ProcessCreate onmatch=”exclude”/> <FileCreateTime onmatch=”include”/> </EventFiltering> </Sysmon>
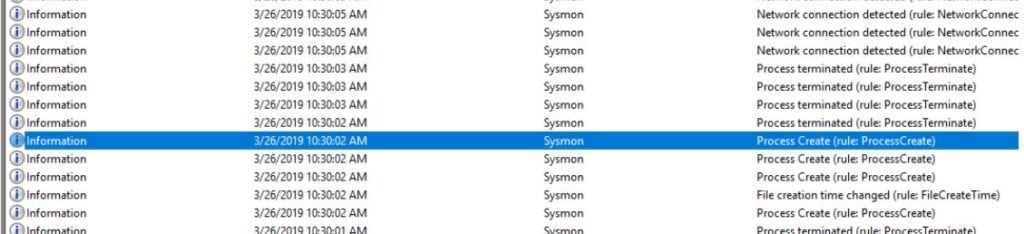
For detailed filtering on a specific event type. You can either choose to include or exclude events based on specific parameters. These parameters will match the rule name in the event log. For example, you may wish to filter a specific process creation event. In the picture below, the process create rule name is highlighted. On the far right is the statement (rule: ProcessCreate). This is the rule name you will use for filtering.
You will want to begin by excluding known false positives. These exclusions will be in categories by event type. To place comments in the config.xml file, utilize the <!-- --> to begin and end a comment block.
Let’s look at an example process create event filter. The first item is the statement that tells us this is the filter for process create events. We are going to exclude any process create event that matches the criteria below from being logged.
<ProcessCreate onmatch="exclude">
First, we are going to exclude by integrity level of the executing process. Starting with Windows Vista, Microsoft introduced a security feature in to the process known as integrity levels. There are four integrity levels, low, medium, high, and system. It is not possible for a processes with a lower integrity level to open a handle with full access to a process with a higher integrity level. This stops attacks such as dll injection without privilege escalation. In this case, we are excluding reporting on actions taken by processes with system level integrity from reporting, assuming they are trusted.
<IntegrityLevel>System</IntegrityLevel>
Next, we might exclude chatty applications from reporting by the process name or image. When using the “contains” operator, we no longer need the entirety of the path. Note that there are both images and parent images in a process event. The parent image often calls to a second process.
<Image condition="contains">C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe</Image> <ParentImage condition="contains">C:\Program Files (x86)\Google\Update\GoogleUpdate.exe</ParentImage>
Finally, we can also filter based on what the command line itself contains. Be aware, Sysmon does not capture every command executed, but only captures those applicable to the creation of a process. Like the image, there is both a command line and parent command line.
<CommandLine condition="contains">C:\Windows\system32\wbem\wmiprvse.exe -secured -Embedding</CommandLine> <ParentCommandLine condition="contains">C:\Windows\system32\SearchIndexer.exe /Embedding</ParentCommandLine>
Finally, we will close the process create section and move on to another event type.
</ProcessCreate>
Some example filters for other types of events are shown below.
<FileCreateTime onmatch="exclude"> <Image condition="end with">chrome.exe</Image> <Image condition="end with">firefox.exe</Image> <Image condition="end with">outlook.exe</Image> <Image condition="end with">iexplore.exe</Image> <Image condition="contains">C:\Windows\system32\msiexec.exe</Image> <Image condition="contains">C:\Windows\syswow64\MsiExec.exe</Image> </FileCreateTime>
<NetworkConnect onmatch="exclude"> <DestinationIp condition="contains">169.254</DestinationIp> <DestinationIp condition="contains">255.255.</DestinationIp> <DestinationIp condition="contains">239.255.</DestinationIp> <DestinationIp condition="begin with">10.</DestinationIp> <DestinationIp condition="contains">127.0.</DestinationIp> <DestinationIp condition="contains">0:0:0</DestinationIp> <!--<Image condition="end with">iexplore.exe</Image> --> <!--<Image condition="end with">chrome.exe</Image> --> <Image condition="end with">excel.exe</Image> <Image condition="end with">winword.exe</Image> <Image condition="end with">lms.exe</Image> <Image condition="end with">onenote.exe</Image> <Image condition="contains">C:\Program Files\Mozilla Firefox\firefox.exe"</Image> <Image condition="contains">C:\Program Files\Mozilla Firefox\firefox.exe</Image> <DestinationPortName condition="end with">dhcpv6-client</DestinationPortName> <DestinationPortName condition="end with">epmap</DestinationPortName> <DestinationPortName condition="end with">llmnr</DestinationPortName> <DestinationPortName condition="end with">netbios-dgm</DestinationPortName> <DestinationPortName condition="end with">netbios-ns</DestinationPortName> <DestinationPortName condition="end with">netbios-ns</DestinationPortName> <SourcePortName condition="end with">llmnr</SourcePortName> <SourcePortName condition="end with">epmap</SourcePortName> <SourcePortName condition="end with">ws-discovery</SourcePortName> <SourcePortName condition="end with">ssdp</SourcePortName> </NetworkConnect>
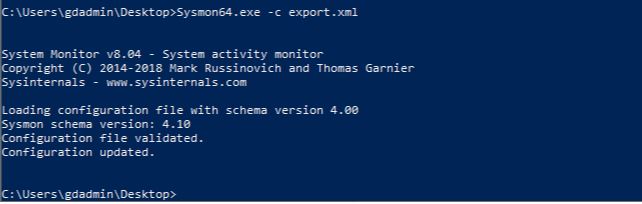
To apply the filter to the Sysmon configuration simply type Sysmon -c c:\thepathtoyourconfig.xml. See the example below.
Sysmon can be configured as much as necessary to fit your environment. For some additional recommendations on preconfigured filters, check out this file at GitHub. Happy hunting!