Despite being an essential piece of the Sysadmin toolbox, Network performance management (NPM) can be a bit of a mystery for many IT professionals.
Part of the issue is that the NPM toolset is vast, and can be vague—device monitoring, packet and flow analysis, and log analysis are all part of the equation.
Another, is that there is no singular use case for NPM tools—they can be used to monitor and troubleshoot network issues, they can be used to plan network capacity, and last but not least, they can even be used for security monitoring.
Unsurprisingly, this variety of technologies and use cases causes some confusion when researching NPM tools. It can be hard to know what tools address which use cases, and which is the best tool for the job.
For that reason, Enterprise Management Associates (EMA) have put together a new research report to help assuage the confusion in the NPM market. EMA’s report, “Network Performance Management Strategies for the Digital Enterprise.”
For this report, EMA’s research team surveyed approximately 250 IT professionals and conducted phone interviews to identify best practices and success strategies for NPM solutions. What they found, was a growing number of use cases, including increasingly security-oriented use of NPM tools.
You can download a 39-page executive summary of the report here, or read on for a brief summary of its findings.
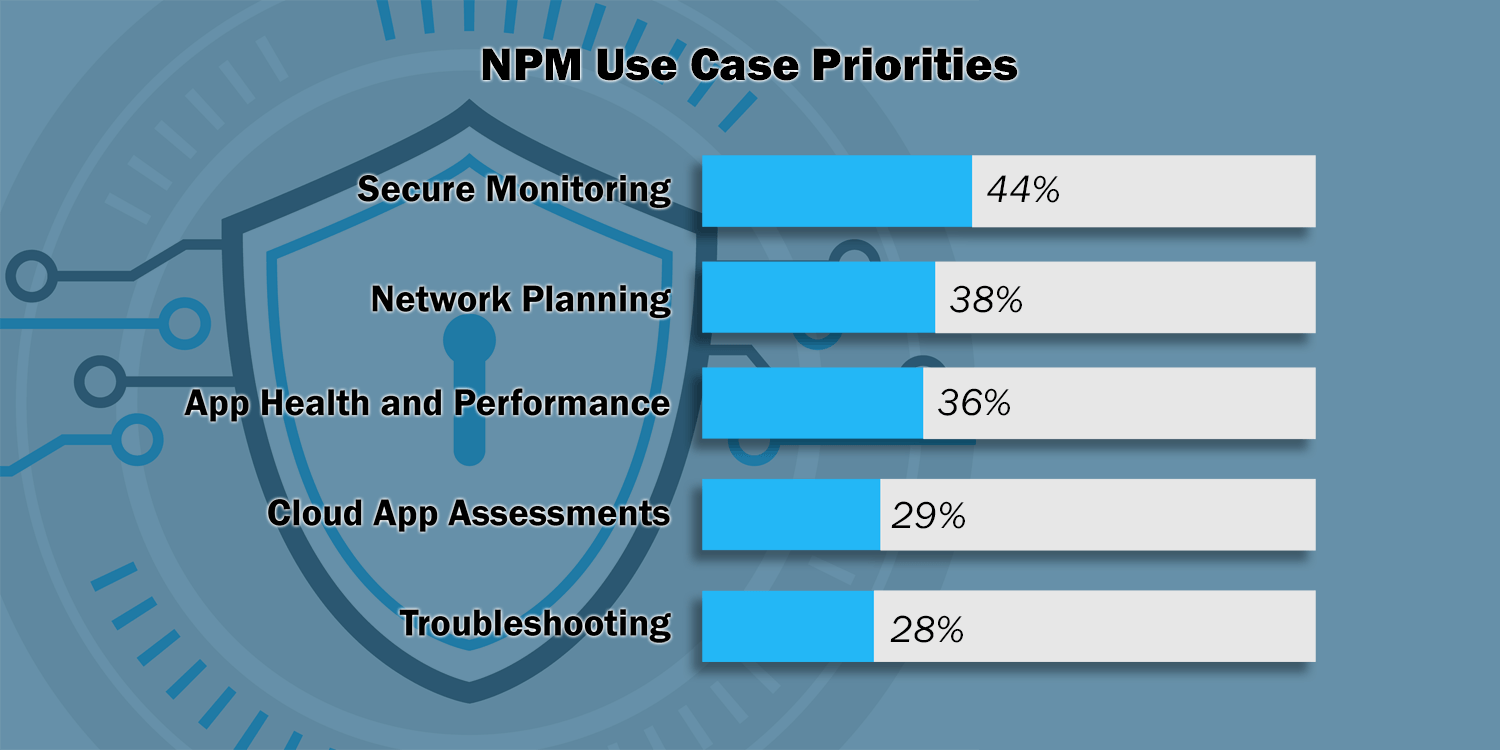
IT Pros Cite Security as #1 Influencer of NPM Tool Strategies
In a surprising result, when asked which technology initiatives were most influential on their NPM tool strategies, 36 percent of IT pros cited Security, making it the #1 influencer in the poll, just above cloud connectivity and Data Center SDN. This result was primarily driven by IT Analytics professionals, 59% of whom cited security as the top influencer. On the other hand, just 19 percent IT management tool architecture and engineering group, cited security as a top influencer of their NPM tool strategy, which suggests that those who actually buy and implement NPM tools don’t have security top-of-mind.
While this result was somewhat unexpected, many in the NPM space have been calling for greater use of the tools for security purposes, including writers at this blog.
Using network performance monitoring tools for security purposes is primarily a tertiary use case to the IT teams, but it has been an increasingly popular use of the tools in recent years. Many security attacks like DoS/DDoS and viruses cause traffic anomalies including unusual spikes in network traffic and a high number of failed connections. Historically analyzing and trending traffic patterns can be useful in proactively identifying and repelling these attacks. By leveraging real-time alerts and thresholds (based on the volume of traffic, failed connections per host, top senders/receivers), the administrator can ensure rapid response to security issues.
Traffic Volume Analysis and Visualization are Seen as Top Priorities for Features and Functions
Unsurprisingly, a plurality of IT pros voted for Traffic Volume Analysis (26%) and Network Traffic Visualization (24%) as the top NPM tool functions and features. According to EMA “these features help enterprises answer two key questions: How much traffic is on my network? Who is communicating on my network? Correlating the answers to these two questions can give a network manager a good overview of the health and performance of a network.”
It’s likely that this result comes from the desire to have a healthy network. Monitoring network traffic is one of the most critical aspects of network management. Without comprehensive insight into what traffic is consuming bandwidth, it is not possible to ensure proper availability for business-critical services and applications. So users are looking to meet SLAs, and to keep the network up and running, and to be aware of what’s happening, where traffic spikes, etc. But there is a security use case for this too. It’s very common for traffic monitoring tools to help distinguish between normal traffic patterns and suspicious ones. With viruses and malware often consuming out of the ordinary amounts of bandwidth, monitoring bandwidth utilization can also be invaluable in identifying security anomalies.
In addition to the security implications of NPM, EMA’s report also includes research results on:
- Essential network data: What data sources (packets, flows, device metrics, etc.) do enterprises apply to different NPM use cases
- Multi-tool correlation: How IT organizations assemble a toolset and correlate insights across discrete tools
- Operational insight: How IT organizations correlate NPM-based insights with application performance, end-user experience, and security
- Technology initiatives: Which IT initiatives and network technology projects are impacting NPM tool strategies
- Tool Requirements: What NPM tool features and functions deliver maximum value to enterprises
You can download a 39-page summary of the research results here.
